Adapting to the Threat Landscape: Why Outdated Systems Fail to Protect Against Modern Cyberattacks
We’re living in a technology renaissance, where it’s constantly changing and becoming more innovative, including cyberattacks. The more you watch the news, the more you will hear about security breaches among every type of company, big and small, due to a lack of cyber security measures. So, why does this keep happening? Antiquated systems can drive vulnerabilities leaving a perfect setup for hackers to exploit. This is because the technology that is antiquated wasn’t built to withstand today’s sophisticated hackers.
One of the main reasons why cyberattacks continue to occur is due to the ever-evolving nature of technology. As technology advances, so do the methods and tactics used by hackers. This means that what may have been a secure system or process in the past, may no longer be sufficient in protecting against modern cyber threats.
Additionally, many companies fail to prioritize cybersecurity measures until it’s too late. This can be due to a lack of awareness or understanding of the potential impact and consequences of a cyberattack. However, the reality is that the cost of recovering from a cyberattack can be much higher than investing in preventive measures.
Moreover, companies may also overlook cybersecurity as they focus on other business priorities such as growth and profitability. However, neglecting cybersecurity can have a detrimental effect on a company’s reputation and bottom line in the long run.
It’s important for companies to understand that implementing strong cyber security measures is no longer an option, but a necessity in today’s tech-driven world. This includes regularly updating systems, investing in advanced security software, and educating employees on best practices for protecting sensitive information.
As hackers continue to develop their skills, designing new ways to take advantage of exposures your technology has not adapted if it’s antiquated. The inability to be notified by your systems has been compromised and quickly intervened when your hackers have the upper hand. In these instances, companies big and small become reactive and quickly realize that putting things off or doing it in-house to save money is not the way to avoid such a disaster. When a cyberattack happens, now you are doing reactive problem solving, which puts everything else that was a priority on the back burner, while you now try to deal with this issue at hand. It’s clever if you really think about it. Companies that are being complacent can quickly become easy targets for hackers. Espionage is not a new concept; militaries around the world have been using this tactic for years. Hackers are just taking a page out of the military’s playbook and frankly one-upping them.
Therefore, it’s vital for companies to stay proactive and continuously update their cybersecurity measures to keep up with the changing threat landscape. Regular vulnerability assessments, penetration testing, and employee training can also help identify any weaknesses in a company’s systems and processes.
Cyberattacks continue to occur due to the ever-evolving nature of technology, neglecting cybersecurity measures, and complacency. To prevent being a victim of a cyberattack, companies must prioritize and invest in strong cybersecurity measures that are continuously updated to keep up with the changing threat landscape. This is not only crucial for protecting sensitive information but also for maintaining a company’s reputation and bottom line.
You may be thinking, how can a hacker know if we did or did not invest in technology? I would ask you the same thing. How easy is it to look at a client list on most software and cyber websites? It’s even easier to just try to break into your systems; they will keep trying until they find your exposure. Still don’t believe me. I’ll also let you in on a secret. Code is written by people, and people are flawed. If someone knows how to exploit those flaws, they can find a way into your systems. This is why it’s crucial for companies to not only invest in cybersecurity measures but also continuously test and update them to stay one step ahead of hackers.
Code writing is important; code-breaking is fun.
I remember back in college reading a very famous book by David Halberstam, “The Making of a Quagmire.” It was my first introduction to a term and tactic that has stuck with me since Guerrilla warfare. I can’t tell you I’m a history buff, but I do enjoy history. It’s described as the type of warfare fought by irregulars in fast-moving, small-scale actions against military and police forces, and on occasion, against rival insurgent forces, either independently or in conjunction with a larger political-military strategy. This strategy was impactful and deadly during the Vietnam war and is similar to the cyber-attacks we see today – silent but deadly.
It’s guerrilla warfare on our already vulnerable cyber landscape. As a business owner myself, I can relate to having too many things to do and not enough time in the day to do them. It’s easy to prioritize the everyday tasks, phone calls, video meetings while putting some of the larger undertakings on the back burner. You know they are there; it’s just not top of mind until something happens.
It’s very important to look at how we spend our time and resources. You have to make sure your technology is capable of protecting your assets, data, client information, and company information as well as still being the right solution for your business and team. Have you designated the budget and actual time to analyze your current technology as well as change what is no longer working?
Investing in cybersecurity measures and regularly updating them is not just a business expense; it’s an investment in the future of your company. It’s important to continuously evaluate and improve these measures to stay ahead of cyber threats, protect sensitive information, maintain reputation, and ultimately preserve profitability. In this age of technology, strong cybersecurity measures are no longer optional but essential for business success. So, take the time to assess your company’s cybersecurity measures and make necessary changes to ensure a safe and secure future for your company. Remember, being proactive is always better than being reactive.
Invest in robust cybersecurity measures now to prevent the costly repercussions of a cyberattack later, as wisely stated by Benjamin Franklin: “An ounce of prevention is worth a pound of cure.” Your company’s reputation and financial health will benefit in the long term. Remember, it’s not a matter of if but when; stay prepared and proactive.
Technology budgets are often dedicated to maintaining legacy systems rather than upgrading and protecting your data and information.
It’s no longer about a hacker guessing your passwords or sending you a phishing email. Hackers are far more sophisticated and continue to improve their skills. They are not looking to guess your password and gain access to user-level information; they are looking for your system’s vulnerabilities and Zero-Day Vulnerabilities. This may be the first time you have heard this term, and if so, I hope to etch this in your memory forever. If you use any kind of technology for your business, you’ll need to stay on top of this. A zero-day vulnerability is a software security flaw that is known to the software vendor but doesn’t have a patch in place to fix the flaw, leaving you exposed to someone just looking for an opportunity. Essentially, it’s a known flaw without a patch. Antiquated technology will have fewer patches, more opportunities for exposure, which cannot easily fend off today’s hackers.
Technology is evolving at an incredible pace, and it’s essential for businesses to stay current with their systems and software. Regularly evaluate your technology, prioritize security updates, and invest in new and secure solutions to protect your company from cyber threats. Remember, outdated technology is a ticking time bomb waiting to be exploited by hackers.
In summary, cybersecurity measures are crucial for every business in today’s digital world. Companies must invest in robust and continuously updated security measures to stay ahead of hackers who are constantly evolving their tactics. It’s not enough to just have strong cybersecurity measures in place; companies must also regularly evaluate, update, and prioritize these measures to ensure protection from cyber threats. Remember, being proactive is always better than being reactive when it comes to cybersecurity. Invest in the future of your company by investing in top-notch cybersecurity measures and staying informed about the latest threats and vulnerabilities. Don’t let outdated technology leave your company vulnerable to cyberattacks; stay current, secure, and successful. So, I urge you to take action now and prioritize cybersecurity for the long-term success of your business. Your clients, employees, and company’s reputation will thank you. Remember, code writing may be important, but code-breaking is not fun when it’s your business on the line. Stay updated and stay secure. So, invest in cybersecurity now to protect your company’s future.
Staying ahead of cyber threats requires a combination of proactive measures and continuous evaluation and updating of security measures. By prioritizing cybersecurity in your business, you are not only protecting your assets and sensitive information, but also safeguarding the trust of your clients, employees, and stakeholders. It’s not just about investing in technology; it’s about investing in the longevity and success of your company. So don’t wait for a cyberattack to happen; take action now and prioritize cybersecurity as a crucial aspect of your business strategy. The stakes are high, it’s better to be prepared than to suffer the consequences of a cyberattack. Stay informed, stay proactive, and stay secure. Your business and its future depend on it.
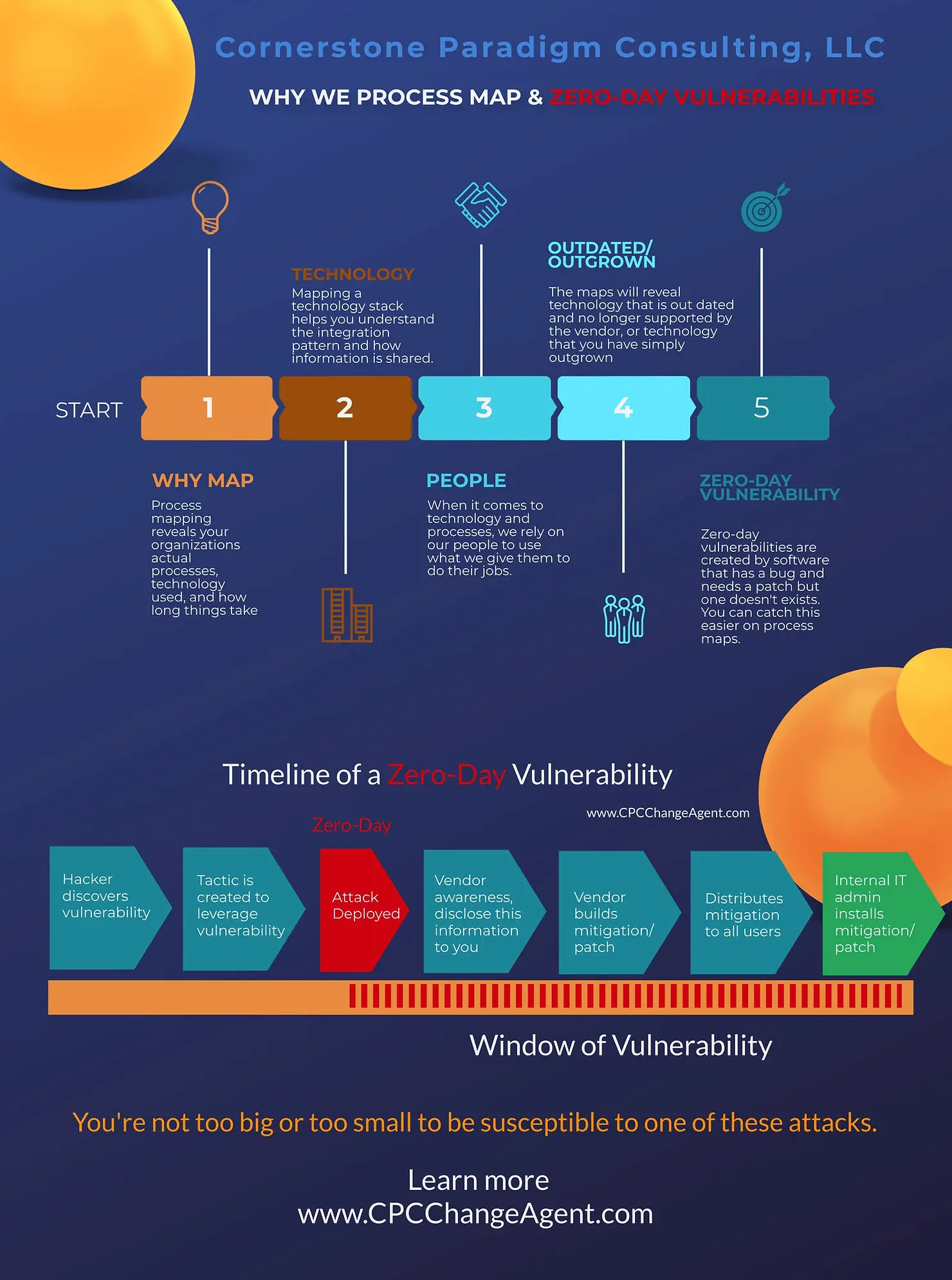 My suggestion:
My suggestion:
- Go through a process map
- Review your technology stack and your push and pull
- Look for your digital exposures on the map
- Find and replace antiquated technology with technology built to defend
- Review your cyber plan
- Test the plan often